記事
チュートリアル
インタラクティブ ガイド
DevSecOps ツール
DevOps ワークフローを保護する DevSecOp ツール

Kev Zettler
フルスタック Web 開発者
ソフトウェア会社は最善を尽くしていますが、セキュリティ侵害は依然として発生しています。2000 年以降、推定 35 億人が個人データ盗難の被害に遭っています。問題の一部は、ソフトウェア アプリケーションのコードベースの規模と複雑さが増すにつれて、セキュリティの脆弱性とエクスプロイトの攻撃対象領域も広がるという点です。
さらに、ソフトウェア開発チームと IT チーム間のプロセスを自動化して統合する DevOps アプローチを採用する組織が増えるにつれ、従来のセキュリティ ツールでは間に合わなくなることも多くなります。今日の開発者は、開発ワークフローのあらゆる段階にセキュリティ対策を組み込む必要があります。DevOps ワークフローのセキュリティに関して言えば、このプラクティスを DevSecOps と呼びます。
DevSecOps とは?
DevSecOps は、継続的インテグレーション、継続的デリバリー、継続的デプロイのパイプラインにセキュリティを統合するプラクティスです。ソフトウェア セキュリティに DevOps の価値を適用することで、セキュリティ検証が開発プロセスの有効な一部分として統合されます。
DevOps と同様に、DevSecOps は、プロジェクト管理ワークフローと自動化された IT ツールを組み合わせた組織的かつ技術的な方法論です。DevSecOps では、アクティブなセキュリティ監査とセキュリティ テストをアジャイル開発ワークフローと DevOps ワークフローに統合することで、セキュリティを最終製品に適用するのではなく製品自体に組み込みます。
DevSecOps を実装するには、チームは次の作業を行う必要があります。
- ソフトウェア コードの脆弱性を最小限に抑えるために、ソフトウェア開発ライフサイクル全体にセキュリティを導入する。
- 開発者や運用チームを含む DevOps チーム全体に、セキュリティのベスト プラクティスに従う責任を共有させる。
- セキュリティ コントロール、ツール、プロセスを DevOps ワークフローに統合することで、ソフトウェア デリバリーの各段階で自動化したセキュリティ チェックを有効にする。
DevSecOps では、標準的な DevOps パイプラインの各フェーズ (プラン、ビルド、テスト、デプロイ、運用、観察) にセキュリティを適用する必要があります。
"継続的" は DevOps パイプラインの差別化された特性です。これには、継続的インテグレーション、継続的デリバリー/デプロイ (CI/CD)、継続的なフィードバック、継続的な運用が含まれます。1 回限りのテストや予定デプロイではなく、各機能は継続的に実行されます。
関連資料
Bitbucket Cloud 向け Snyk の詳細
ソリューションを見る
Bitbucket Cloud 向け Snyk の入手
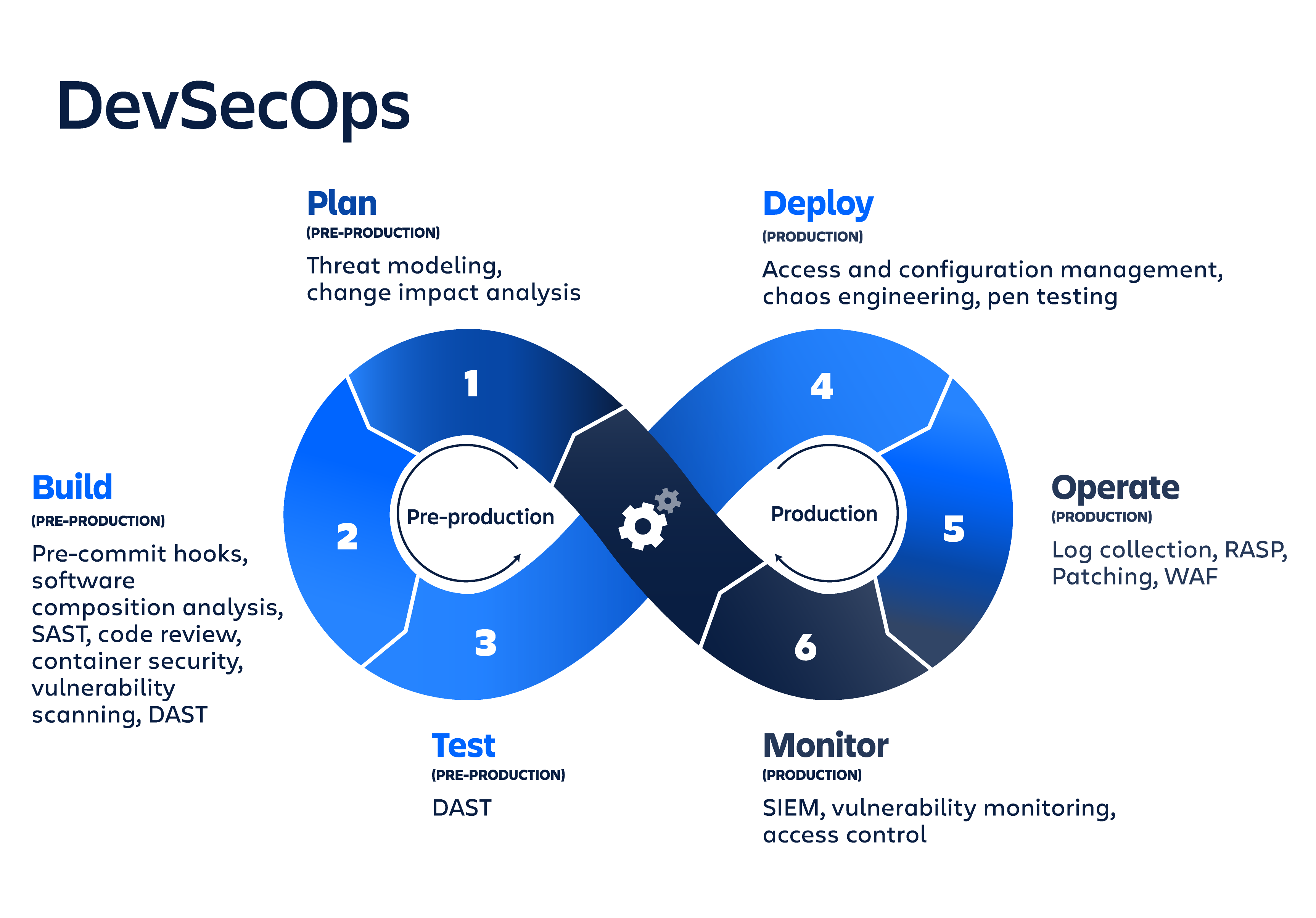
計画
ビルド
構築フェーズは、開発者がソース リポジトリにコードをコミットした時点で開始されます。DevSecOps ビルド ツールは、ビルド出力アーティファクトに対する自動セキュリティ分析に重点を置いています。重要なセキュリティ プラクティスには、ソフトウェア コンポーネント分析、静的アプリケーション ソフトウェア テスト (SAST)、ユニット テストが含まれます。ツールを既存の CI/CD パイプラインにプラグインして、これらのテストを自動化できます。
開発者はサードパーティのコード依存関係を定期的にインストールして利用しますが、そのソースは未知または信頼できない可能性があります。外部コードの依存関係には、脆弱性やエクスプロイトが偶発的に含まれていたり、悪意を持って組み込まれていたりする可能性があります。構築フェーズでは、これらの依存関係をレビューして、セキュリティの脆弱性がないかをスキャンすることが重要です。
構築フェーズ分析を実行するための有名なツールには、OWASP Dependency-Check、SonarQube、SourceClear、Retire.js、Checkmarx、 Snyk などがあります。
コード フェーズ用の DevSecOps ツールは、開発者がより安全なコードを記述するのに役立ちます。コード フェーズの重要なセキュリティ プラクティスには、静的コード分析、コード レビュー、コミット前フックが含まれます。
セキュリティ ツールを開発者の既存の Git ワークフローに直接プラグインすると、コミットとマージのたびにセキュリティ テストまたはレビューが自動でトリガーされます。これらのツールは、さまざまなプログラミング言語と統合開発環境をサポートしています。より一般的なセキュリティ コード ツールには、Gerrit、Phabricator、SpotBugs、PMD、CheckStyle、Find Security Bugs などがあります。
テスト
テスト フェーズは、ビルド アーティファクトが作成されて、ステージング環境またはテスト環境に正常にデプロイされた後にトリガーされます。包括的なテスト スイートの実行にはかなりの時間がかかります。このフェーズはフェイル ファストして、より高価なテスト タスクが最後に残されるようにする必要があります。
テスト フェーズでは動的アプリケーション セキュリティ テスト (DAST) ツールを使用して、ユーザー認証、承認、SQL インジェクション、API 関連のエンドポイントなどのライブ アプリケーション フローを検出します。セキュリティ重視の DAST では、OWASP トップ 10 に記載されている問題など、重大度の高い既知の問題リストと照らし合わせてアプリケーションが分析されます。
言語エコシステムのためのさまざまな機能とサポートを提供する、多数のオープン ソースと有料のテスト ツールが利用可能です (BDD Automated Security Tests、JBroFuzz、Boofuzz、OWASP ZAP、Arachi、IBM AppScan、GAUNTLT、SecApp suite など)。
デプロイ
ここまでのフェーズが正常に完了したら、ビルド アーティファクトを本番環境にデプロイします。デプロイ フェーズで対処するセキュリティ領域は、本番システムに対してのみ発生するセキュリティ領域です。たとえば、本番環境と以前のステージング環境と開発環境の構成の相違点については、徹底的なレビューが必要です。本番環境の TLS 証明書と DRM 証明書については、今後の更新のために検証とレビューを行う必要があります。
デプロイ フェーズでは、実行中のシステムから情報を抽出して期待どおりに動作するかどうかを判断する、Osquery、Falco、Tripwire などのランタイム検証ツールが活躍します。また、組織は、カオス エンジニアリングの原則に従ってシステム上で実験することで、混乱した状況に耐えるシステムの能力に対する信頼を築けます。サーバーのクラッシュ、ハード ドライブの障害、ネットワーク接続の切断など、実際のイベントをシミュレートできます。Netflix の有名な Chaos Monkey ツールは、カオス エンジニアリングの原則を実践するツールです。また、Netflix は不適切に構成されたインフラストラクチャ セキュリティ グループの違反や脆弱性を探し、脆弱なサーバーを切断する Security Monkey ツールを利用しています。
DevSecOps サイクルのリリース フェーズでは、アプリケーション コードと実行可能ファイルは既に徹底的にテスト済みであるはずです。このフェーズでは、ユーザー アクセス制御、ネットワーク ファイアウォール アクセス、シークレット データ管理などの環境構成値を調べて、ランタイム環境インフラストラクチャのセキュリティ保護に重点を置きます。
最小権限の原則 (PoLP) は、リリース フェーズの重要な関心事項です。PoLP は、すべてのユーザー、プログラム、またはプロセスが、それぞれの役割を果たすための最小限のアクセス権を持っていることを意味します。これには、所有者のアクセスを制限するための API キーとアクセス トークンの監査が含まれます。この監査を行わないと、システムの意図しない領域にアクセスできるキーを攻撃者が見つけてしまう可能性があります。
構成管理ツールは、動的インフラストラクチャの静的構成を可視化できるという点で、リリース フェーズにおけるセキュリティの重要な要素です。したがって、システム構成を監査してレビューできます。構成は変更不可能になり、構成管理リポジトリへのコミットによってのみ更新できます。一般的な構成管理ツールには、Ansible、Puppet、HashiCorp Terraform、Chef、Docker などがあります。
セキュリティ コミュニティは、CIS (Center for Internet Security) ベンチマークや NIST 構成チェックリストなど、インフラストラクチャを強化するためのベスト プラクティスに関するガイドラインと推奨事項を提供します。
観察
アプリケーションが本番環境でデプロイされて安定化されると、追加のセキュリティ対策が必要になります。企業は自動化されたセキュリティ チェックとセキュリティ監視ループによって、ライブ アプリケーションの攻撃やリークを監視して観察する必要があります。
RASP (Runtime application self-protection: ランタイム アプリケーションのシステム保護) は、インバウンドのセキュリティ脅威をリアルタイムで自動で識別してブロックする技術です。RASP は攻撃の侵入を監視するリバース プロキシとして機能して、明示的な条件に応じて人間の介入なしにアプリケーションを自動で再構成することを目的としています。
専門の内部または外部のチームがペネトレーション テストを実行して意図的にシステムを侵害することにより、エクスプロイトや脆弱性を検出できます。もう 1 つのセキュリティ手法は、セキュリティ上のエクスプロイトや脆弱性を報告した外部の個人に対して謝礼を行う、バグ報奨金プログラムを提供することです。
セキュリティ監視では、アナリティクスを使用して重要なセキュリティ関連の指標を計測して監視します。たとえば、これらのツールを通じて、ユーザー アカウント アクセス フォームやデータベース エンドポイントなど、機密性の高いパブリック エンドポイントへのリクエストにフラグを立てます。一般的なランタイム防御ツールの例としては、Imperva RASP、Alert Logic、Halo などがあります。
結論
プロセスを進化させて新しいツールを採用する開発チームが増えるにつれて、セキュリティへの綿密な取り組みが必要になります。DevSecOps は循環的なプロセスであり、新しいコードのデプロイごとに継続的なイテレーションと適用を行う必要があります。エクスプロイトと攻撃者は絶えず進化しており、近代のソフトウェア チームも同様に進化することが重要です。
DevSecOps テストは、Bitbucket Pipelines でテストを自動化することから始めるとよいでしょう。また、Atlassian Marketplace で入手可能なテスト自動化ツールとリソースも必ずご確認ください。
この記事を共有する
次のトピック
おすすめコンテンツ
次のリソースをブックマークして、DevOps チームのタイプに関する詳細や、アトラシアンの DevOps についての継続的な更新をご覧ください。

DevOps コミュニティ
DevOps ラーニング パス